TCP通信
访问量:2779
创建时间:2020-12-29
TCP/IP 五层模型
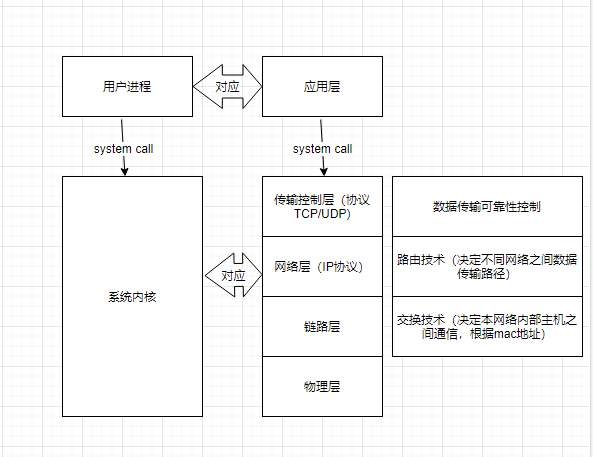
套接字 :端口到端口的一对组合(含有原IP地址,源tcp端口,目标IP地址,目标tcp端口)
[root@localhost ~]# netstat -an
Active Internet connections (servers and established)
Proto Recv-Q Send-Q Local Address Foreign Address State
tcp 0 52 192.168.0.86:22 10.1.5.246:49421 ESTABLISHED
tcp6 0 0 192.168.0.86:37008 10.0.0.18:3306 ESTABLISHED
tcpdump抓取三次握手四次挥手
tcpdump 抓取
[root@localhost ~]# tcpdump -nn -i ens192 port 80
tcpdump: verbose output suppressed, use -v or -vv for full protocol decode
listening on ens192, link-type EN10MB (Ethernet), capture size 262144 bytes
#注释:客户端发送syn包到server
14:59:56.837101 IP 192.168.0.86.36984 > 36.152.44.96.80: Flags [S], seq 477800002, win 29200, options [mss 1460,sackOK,TS val 3975098472 ecr 0,nop,wscale 7], length 0
#server回复syn + ack包
14:59:56.866217 IP 36.152.44.96.80 > 192.168.0.86.36984: Flags [S.], seq 1979099966, ack 477800003, win 8192, options [mss 1350,sackOK,nop,nop,nop,nop,nop,nop,nop,nop,nop,nop,nop,wscale 5], length 0
#客户端发送 ack包到server
14:59:56.866280 IP 192.168.0.86.36984 > 36.152.44.96.80: Flags [.], ack 1, win 229, length 0
#上面完成三次握手,下面开始发送请求
14:59:56.866446 IP 192.168.0.86.36984 > 36.152.44.96.80: Flags [P.], seq 1:78, ack 1, win 229, length 77: HTTP: GET / HTTP/1.1
14:59:56.895915 IP 36.152.44.96.80 > 192.168.0.86.36984: Flags [.], ack 78, win 908, length 0
14:59:56.897666 IP 36.152.44.96.80 > 192.168.0.86.36984: Flags [.], seq 1:1281, ack 78, win 908, length 1280: HTTP: HTTP/1.1 200 OK
14:59:56.897699 IP 192.168.0.86.36984 > 36.152.44.96.80: Flags [.], ack 1281, win 251, length 0
14:59:56.898202 IP 36.152.44.96.80 > 192.168.0.86.36984: Flags [P.], seq 1281:2782, ack 78, win 908, length 1501: HTTP
14:59:56.898217 IP 192.168.0.86.36984 > 36.152.44.96.80: Flags [.], ack 2782, win 275, length 0
#下面四次挥手
14:59:56.898395 IP 192.168.0.86.36984 > 36.152.44.96.80: Flags [F.], seq 78, ack 2782, win 275, length 0
14:59:56.907111 IP 36.152.44.96.80 > 192.168.0.86.36984: Flags [P.], seq 2561:2782, ack 78, win 908, length 221: HTTP
14:59:56.907144 IP 192.168.0.86.36984 > 36.152.44.96.80: Flags [.], ack 2782, win 275, options [nop,nop,sack 1 {2561:2782}], length 0
14:59:56.928488 IP 36.152.44.96.80 > 192.168.0.86.36984: Flags [.], ack 79, win 908, length 0
14:59:56.929401 IP 36.152.44.96.80 > 192.168.0.86.36984: Flags [F.], seq 2782, ack 79, win 908, length 0
14:59:56.929431 IP 192.168.0.86.36984 > 36.152.44.96.80: Flags [.], ack 2783, win 275, length 0
请求
[root@localhost ~]# curl www.baidu.com
linux中tcp连接过程与文件描述符
#访问baidu,用8文件描述符,代表tcp连接socket,<>表示输入输出流重定向到8,
[root@oracledb ~]# exec 8<> /dev/tcp/www.baidu.com/80
# > 重定向到文件,>& 8输出到文件描述符8 (&用来跟文件描述符)
[root@oracledb ~]# echo -e "GET / HTTP/1.0\n" 1>& 8
[root@oracledb ~]# cat 0<& 8
HTTP/1.0 200 OK
Accept-Ranges: bytes
Cache-Control: no-cache
Content-Length: 14615
Content-Type: text/html
Date: Tue, 29 Dec 2020 05:51:22 GMT
P3p: CP=" OTI DSP COR IVA OUR IND COM "
P3p: CP=" OTI DSP COR IVA OUR IND COM "
Pragma: no-cache
###省略部分输出###
#关闭socket,$$表示当前程序,进入前程序的fd目录
[root@oracledb ~]# cd /proc/$$/fd
[root@oracledb fd]# ll
total 0
lrwx------ 1 root root 64 Dec 29 13:50 0 -> /dev/pts/0
lrwx------ 1 root root 64 Dec 29 13:50 1 -> /dev/pts/0
lrwx------ 1 root root 64 Dec 29 13:50 2 -> /dev/pts/0
lrwx------ 1 root root 64 Dec 29 13:50 255 -> /dev/pts/0
lrwx------ 1 root root 64 Dec 29 13:51 8 -> socket:[10538347]
[root@oracledb fd]# pwd
/proc/26706/fd
[root@oracledb fd]# exec 8<& -
登陆评论:
使用GITHUB登陆